error
1
2
| swanctl --list-sas
plugin 'sqlite': failed to load - sqlite_plugin_create not found and no plugin file available
|
1
| yum install strongswan-sqlite
|
安装
1
2
3
4
| setenforce 0
vim /etc/sysconfig/selinux
SELINUX=enforcing => SELINUX=disabled
|
https://koji.fedoraproject.org/koji/packageinfo?buildStart=0&packageID=13302&buildOrder=-completion_time&tagOrder=name&tagStart=0#buildlist
ubuntu
sudo apt-get install strongswan-swanctl
vim /etc/swanctl/swanctl.conf
centos
yum install epel-release -y
yum install strongswan
vim /etc/strongswan/swanctl/swanctl.conf
版本
1、通用的配置文件为strongswan.conf,及strongswan.d目录下文件;
2、Used by swanctl and the preferred vici plugin: //推荐使用
需要配置swanctl目录下的文件。主要是swanctl目录下的swanctl.conf文件,如果你保持安装状态的swanctl.conf文件,则需要在swanctl/conf.d目录下增加新的配置文件,默认的swanctl/swanctl.conf文件会包含你新增的配置文件。
3、Used by starter and the deprecated stroke plugin: //过期,不推荐
3.1)配置ipsec.conf。
3.2)配置ipsec.secrets。
3.3)配置ipsec.d下的配置文件。
特别说明:当使用swanctl和starter工具时,需要的配置文件是完全不同的。
1的配置是必须,而2和3的配置你可以选择其中之一。
本文后述的配置均基于swanctl工具。
基本命令
1
2
3
4
5
6
7
8
9
10
| echo 1 > /proc/sys/net/ipv4/ip_forward
ethtool -K eth0 gro off gso off tso off
service strongswan restart
swanctl --load-all
swanctl --list-conns
swanctl --list-sas
swanctl --initiate --child test_child
|
1
2
3
4
5
6
| 在执行 sudo swanctl --load-all 时,遇到
connecting to 'unix:///var/run/charon.vici' failed: Connection refused
Error: connecting to 'default' URI failed: Connection refused
择需要先执行
service strongswan restart
|
服务端转发上网
1
| iptables -t nat -A POSTROUTING -s 100.64.0.0/24 -o eth0 -j MASQUERADE
|
官方配置样例
https://www.strongswan.org/testing/testresults/
网络拓扑
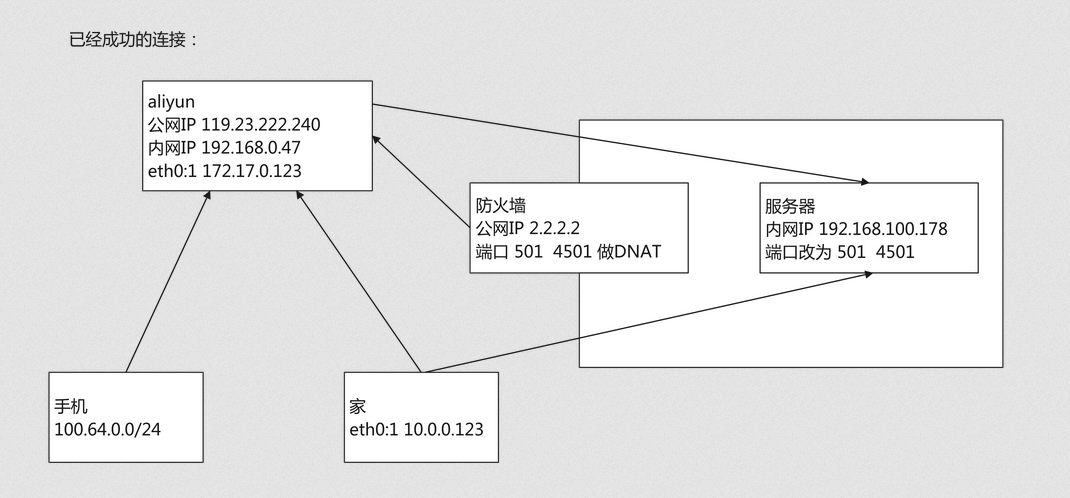
aliyun 配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
| include conf.d/*.conf
connections {
# 防火墙主动连接aliyun可行
# TODO aliyun主动连接防火墙失败???
test {
version = 2
proposals = default
local_addrs = 192.168.0.47
remote_addrs = 2.2.2.2
local {
auth = psk
id = 192.168.0.48
}
remote {
auth = psk
id = 2.2.2.2
}
children {
test_child {
local_ts = 172.17.0.0/24
remote_ts = 192.168.120.0/24
esp_proposals = default
}
}
}
# aliyun主动连接服务器,服务器需要改端口,不然和防火墙冲突,防火墙对端口做DNAT
test178 {
version = 2
proposals = default
local_addrs = 192.168.0.47
local_port = 4500
remote_addrs = 2.2.2.2
remote_port = 4501
local {
auth = psk
id = 119.23.222.240
}
remote {
auth = psk
id = 2.2.2.2
}
children {
test178_child {
local_ts = 172.17.0.0/24
remote_ts = 192.168.100.0/24
esp_proposals = default
}
}
}
# 家连接aliyun
testh {
version = 2
proposals = default
local_addrs = 192.168.0.47
local {
auth = psk
id = 119.23.222.240
}
remote {
auth = psk
id = 192.168.0.105
}
children {
testh_child {
local_ts = 172.17.0.0/24
remote_ts = 10.0.0.0/24
esp_proposals = default
}
}
}
# 手机用 IPSEC IKEv2 PSK 连接aliyun
tests7 {
version = 2
proposals = default
local_addrs = 192.168.0.47
pools = pool1
local {
auth = psk
id = 119.23.222.240
}
remote {
auth = psk
id = 100.64.0.111
}
children {
tests7_child {
local_ts = 172.17.0.0/24
#remote_ts = 100.64.0.0/24
esp_proposals = default
}
}
}
# 失败。 手机用 IPSEC Xauth PSK 连接aliyun,手机的DH-group是modp1024, strongswan 从5.6.1开始取消了modp1024。。。
# https://wiki.strongswan.org/versions/67
tests77 {
version = 1
aggressive = yes
proposals = default
local_addrs = 192.168.0.47
pools = pool1
local {
auth = psk
id = 119.23.222.240
}
remote {
auth = psk
id = 100.64.0.111
}
remote-xauth {
auth = xauth
}
children {
tests77_child {
local_ts = 172.17.0.0/24
remote_ts = 100.64.0.0/24
esp_proposals = default
}
}
}
# cp www.abcxyzkk.xyz_apache/root_bundle.crt /etc/strongswan/swanctl/x509ca/
# cp www.abcxyzkk.xyz_apache/www.abcxyzkk.xyz.crt /etc/strongswan/swanctl/x509/
# cp www.abcxyzkk.xyz_apache/www.abcxyzkk.xyz.key /etc/strongswan/swanctl/private/
# EAP android 客户端 https://download.strongswan.org/Android/
# EAP android 客户端 https://raw.githubusercontent.com/abcdxyzk/abcdxyzk.github.io_files/master/tools/vpn/strongSwan-2.3.3.apk
# EAP 服务端转发上网 iptables -t nat -A POSTROUTING -s 100.64.0.0/24 -o eth0 -j MASQUERADE
# echo 1 > /proc/sys/net/ipv4/ip_forward
testEAP {
version = 2
proposals = default
local_addrs = 192.168.0.47
pools = pool1
local {
certs = www.abcxyzkk.xyz.crt
id = www.abcxyzkk.xyz
}
remote {
auth = eap-mschapv2
id = %any
}
children {
testEAP_child {
#local_ts = 172.17.0.0/24
local_ts = 0.0.0.0/0
#remote_ts = 100.64.0.0/24
esp_proposals = default
}
}
}
# window 用 SHREW IPSec VPN 客户端,https://www.shrew.net/download/vpn/vpn-client-2.2.2-release.exe
# 只能用 ikev1, https://raw.githubusercontent.com/abcdxyzk/abcdxyzk.github.io_files/master/tools/vpn/vpn-client-2.2.2-release.exe
# 公司和阿里云可以连接,但是用手机热点不能连
# 使用野蛮模式aggressive = yes 需要配置 vim /etc/strongswan/strongswan.d/charon.conf
# i_dont_care_about_security_and_use_aggressive_mode_psk = yes
test_window {
version = 1
# aggressive = yes
proposals = default
local_addrs = 192.168.0.47
pools = pool1
local {
auth = psk
id = 192.168.0.48
}
remote {
auth = psk
id = 220.160.201.164
}
children {
test_child {
# local_ts = 192.168.100.0/24
local_ts = 0.0.0.0/0
# remote_ts = 100.64.0.0/24
esp_proposals = default
}
}
}
}
secrets {
ike-testh {
id-vir = 192.168.0.105
secret = abc123
}
ike-tests7 {
id-vir = 100.64.0.111
secret = abc123
}
ike-test {
id-vir = 2.2.2.2
secret = abc123
}
xauth-kk1 {
id = kk1
secret = 123
}
xauth-kk2 {
id = kk2
secret = 123
}
private-www {
file = www.abcxyzkk.xyz.key
}
eap-user {
id = kk3
secret = 123
}
}
pools {
pool1 {
addrs = 100.64.0.0/24
}
}
|
家
TODO 连接防火墙不成功
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
| include conf.d/*.conf
connections {
# 家连接防火墙
test {
version = 2
proposals = default
local_addrs = 192.168.0.105
remote_addrs = 119.23.222.240
local {
auth = psk
id = 192.168.0.105
}
remote {
auth = psk
id = 119.23.222.240
}
children {
test_child {
local_ts = 10.0.0.0/24
remote_ts = 172.17.0.0/24
esp_proposals = default
}
}
}
# 家连接服务器
testh {
version = 2
proposals = default
local_addrs = 192.168.0.105
local_port = 4500
remote_addrs = 2.2.2.2
remote_port = 4501
local {
auth = psk
id = 192.168.0.105
}
remote {
auth = psk
id = 2.2.2.2
}
children {
testh_child {
local_ts = 10.0.0.0/24
remote_ts = 192.168.100.0/24
esp_proposals = default
}
}
}
# linux用EAP连接服务器,要用指定的源IP发起连接才有用。
# swanctl -i --child conn_EAP
hk_EAP {
version = 2
remote_addrs = hk.abc.xyz
remote_port = 4501
local_port = 4502
vips = 0.0.0.0
local {
auth = eap-mschapv2
id = kk_hk
}
remote {
auth = pubkey
id = hk.abc.xyz
}
children {
conn_EAP {
remote_ts = 0.0.0.0/0
rekey_time = 24h
}
}
}
}
secrets {
ike-test {
id-vir = 119.23.222.240
secret = abc123
}
ike-test2 {
id-vir = 2.2.2.2
secret = abc123
}
eap-user_hk {
id = kk_hk
secret = abc123
}
}
|
用win7自带客户端连接aliyun EAP
https://wiki.strongswan.org/projects/strongswan/wiki/WindowsClients/65
win7 默认DH-group 是 modp1024,strongswan已经不在支持
修改 win7 配置 HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters\
增加 NegotiateDH2048_AES256 DWORD 1
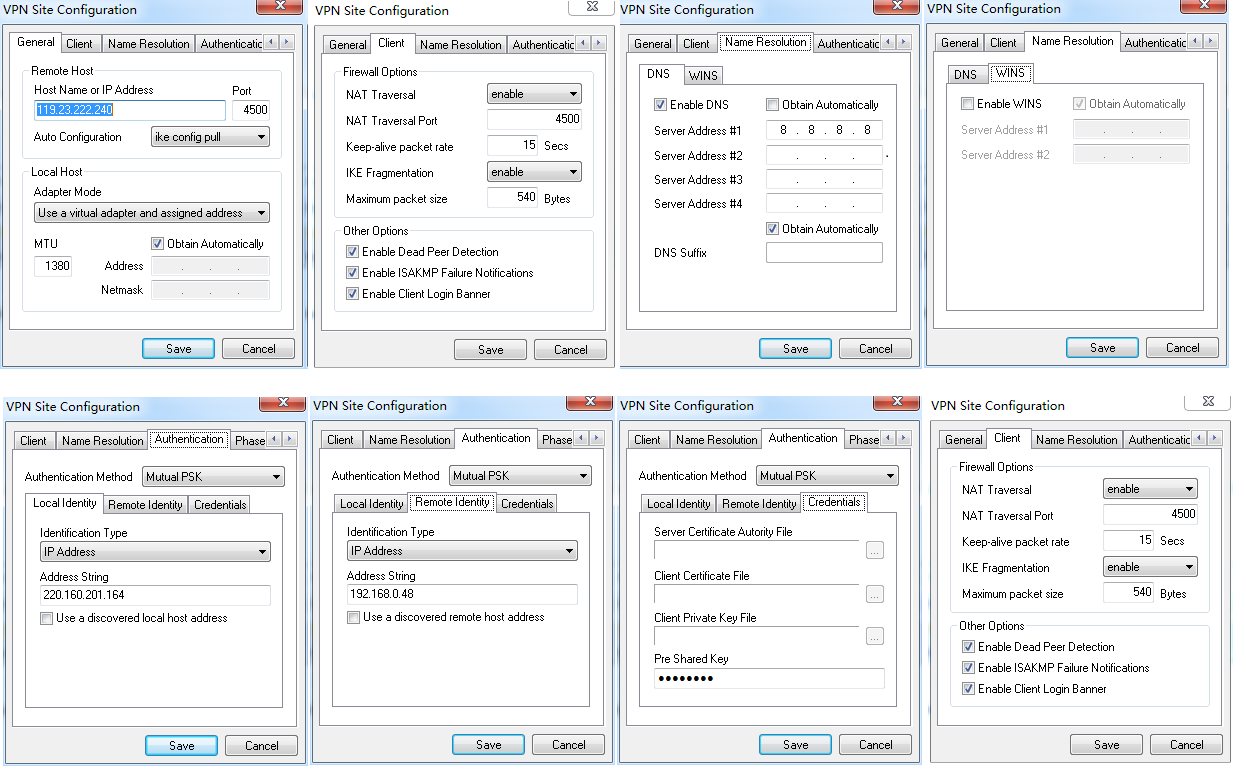
window 用 SHREW IPSec VPN 客户端
http://www.easynetworks.com.cn/forum/faq/detail/id/24
window 用 SHREW IPSec VPN 客户端,https://www.shrew.net/download/vpn/vpn-client-2.2.2-release.exe
只能用 ikev1, https://raw.githubusercontent.com/abcdxyzk/abcdxyzk.github.io_files/master/tools/vpn/vpn-client-2.2.2-release.exe
公司和阿里云可以连接,但是用手机热点不能连
使用野蛮模式aggressive = yes 需要配置 vim /etc/strongswan/strongswan.d/charon.conf
i_dont_care_about_security_and_use_aggressive_mode_psk = yes
服务器
TODO 应为改了端口,不好用手机连服务器
/etc/strongswan/strongswan.d/charon.conf
1
2
3
4
5
6
7
| # port = 500
port = 501
# port_nat_t = 4500
port_nat_t = 4501
|
/etc/strongswan/swanctl/swanctl.conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
| include conf.d/*.conf
connections {
# aliyun 连服务器
test {
version = 2
proposals = default
local_addrs = 192.168.100.178
# local_port = 4501
# remote_addrs = 119.23.222.240
remote_port = 4500
local {
auth = psk
id = 2.2.2.2
}
remote {
auth = psk
id = 119.23.222.240
}
children {
test_child {
local_ts = 192.168.100.0/24
remote_ts = 172.17.0.0/24
esp_proposals = default
}
}
}
# 家连接服务器
testhome {
version = 2
proposals = default
local_addrs = 192.168.100.178
# local_port = 4501
# remote_addrs = 119.23.222.240
remote_port = 4500
local {
auth = psk
id = 2.2.2.2
}
remote {
auth = psk
id = 192.168.0.105
}
children {
test_child {
local_ts = 192.168.100.0/24
remote_ts = 10.0.0.0/24
esp_proposals = default
}
}
}
# cp ~/www.npcable.cn_apache/root_bundle.crt /etc/strongswan/swanctl/x509ca/
# cp ~/www.npcable.cn_apache/www.npcable.cn.crt /etc/strongswan/swanctl/x509/
# cp ~/www.npcable.cn_apache/www.npcable.cn.key /etc/strongswan/swanctl/private/
# EAP 服务端转发上网 iptables -t nat -A POSTROUTING -s 100.64.0.0/24 -o eth0 -j MASQUERADE
# echo 1 > /proc/sys/net/ipv4/ip_forward
testEAP {
version = 2
proposals = default
local_addrs = 192.168.100.178
pools = pool1
local {
certs = www.npcable.cn.crt
id = www.npcable.cn
}
remote {
auth = eap-mschapv2
id = %any
}
children {
testEAP_child {
local_ts = 192.168.100.0/24,192.168.200.0/24,192.168.120.0/24
#local_ts = 0.0.0.0/0
#remote_ts = 100.64.0.0/24
esp_proposals = default
}
}
}
}
secrets {
ike-test {
id-vir = 119.23.222.240
secret = abc123
}
ike-testhome {
id-vir = 192.168.0.105
secret = abc123
}
private-www {
file = www.npcable.cn.key
}
eap-user {
id = kk3
secret = abc123
}
}
pools {
pool1 {
addrs = 100.64.0.0/24
}
}
|
手机配置
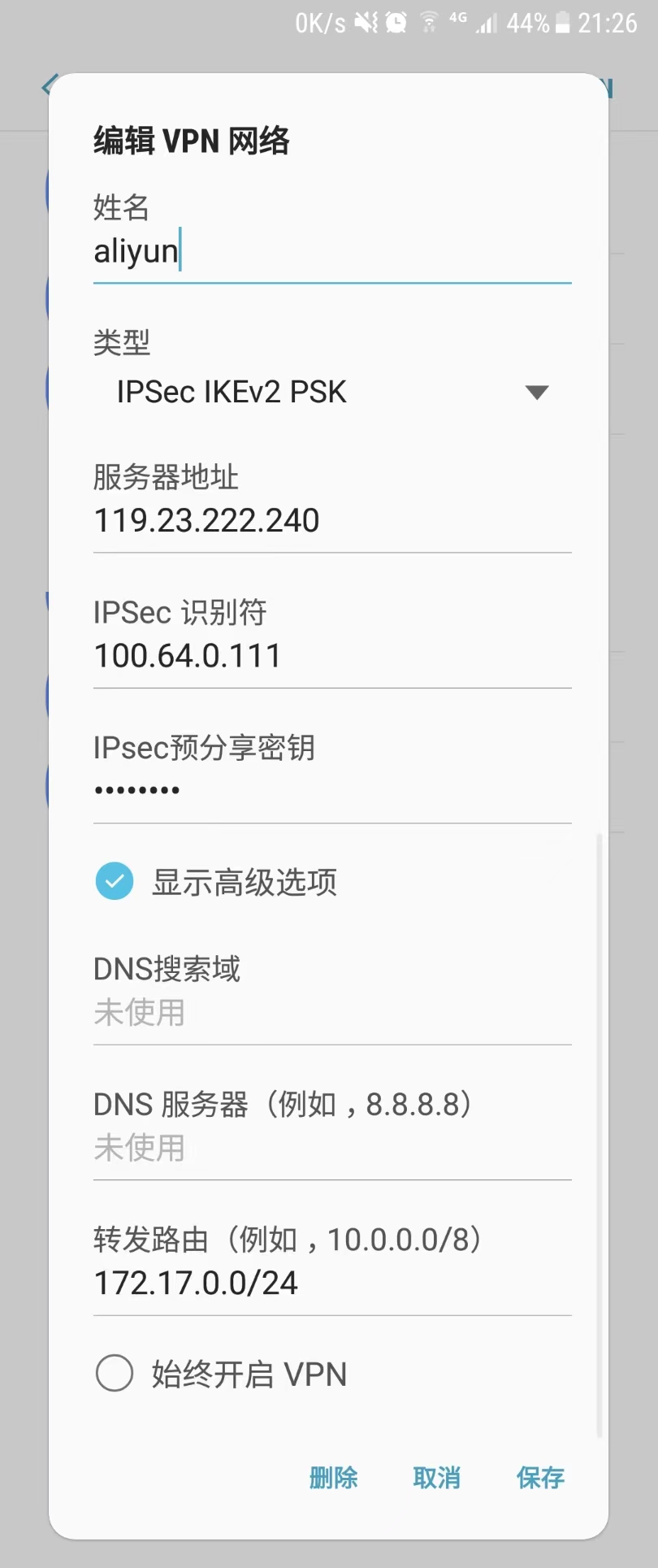
to aliyun ikev2
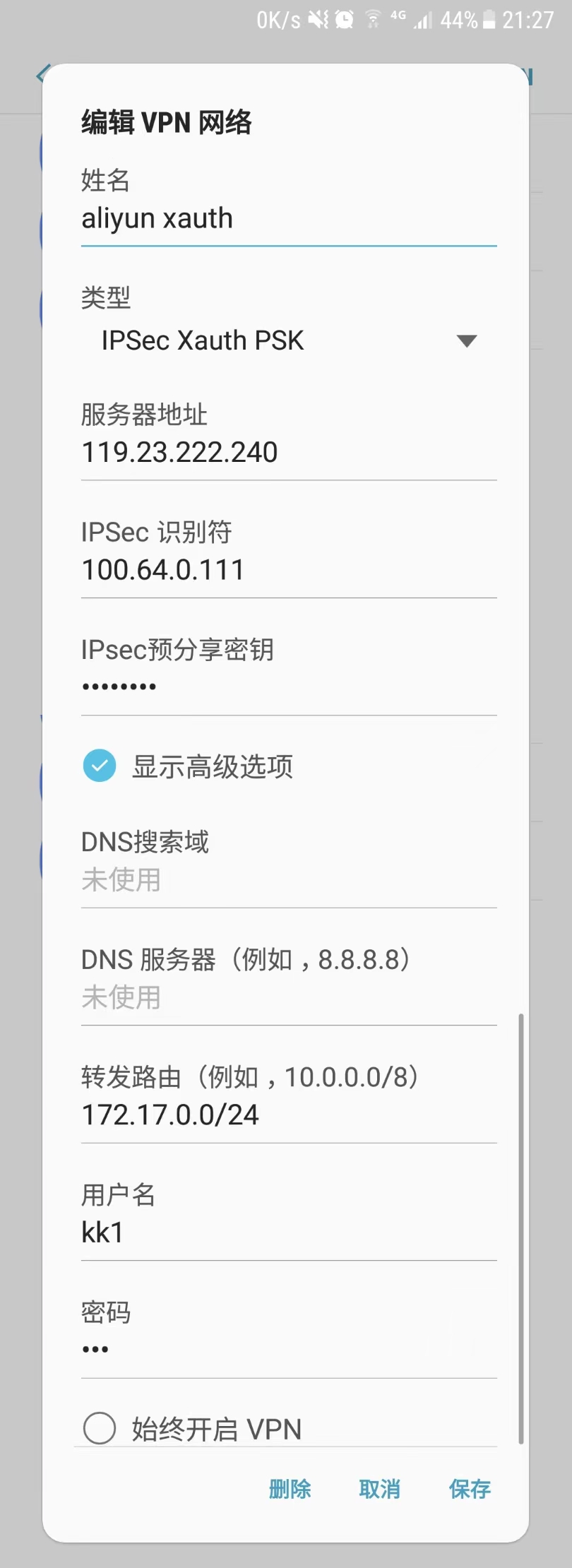
to aliyun xauth
失败。 手机用 IPSEC Xauth PSK 连接aliyun,手机的DH-group是modp1024, strongswan 从5.6.1开始取消了modp1024。。。
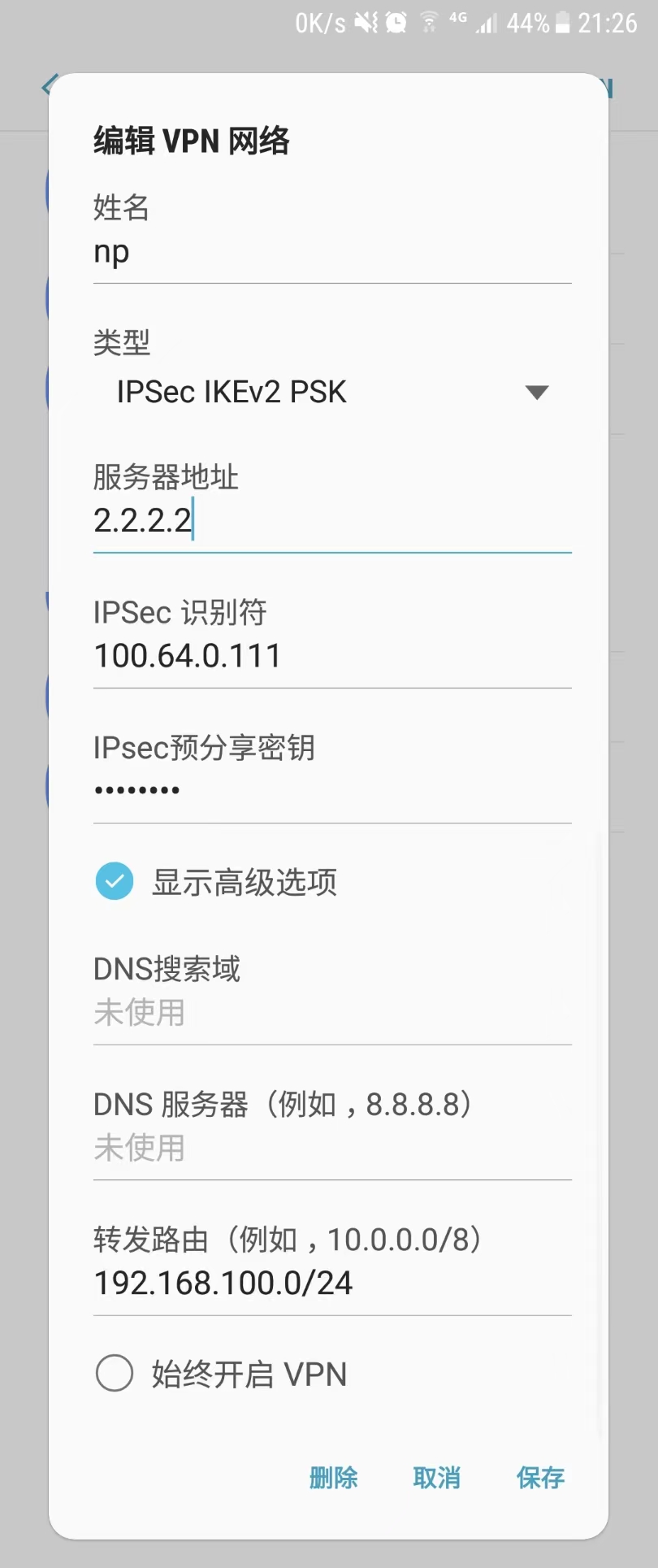
to firewall 不成功
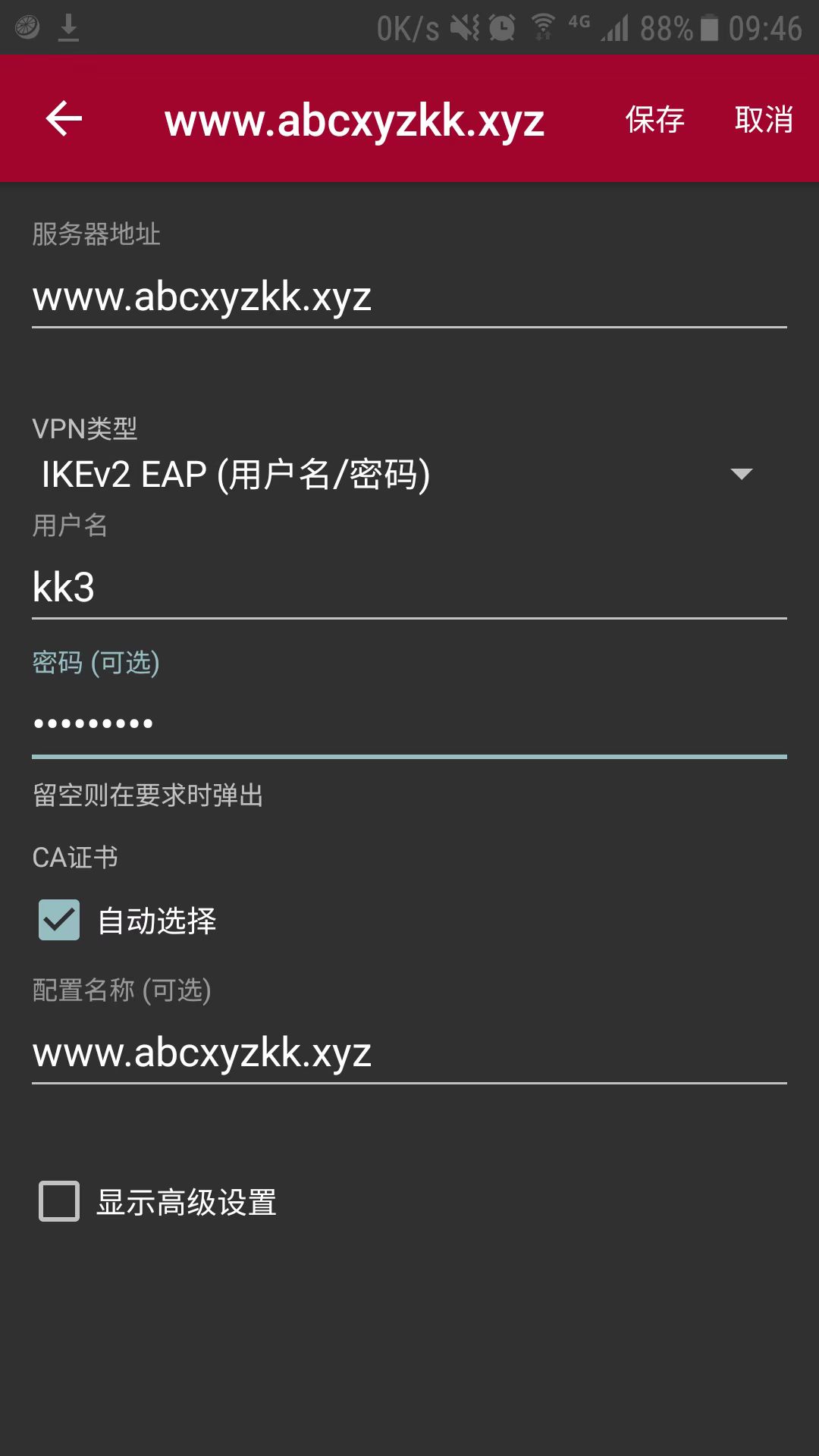
EAP
防火墙配置
DH-group 要改成 group14 及以上,太低strongswan不认
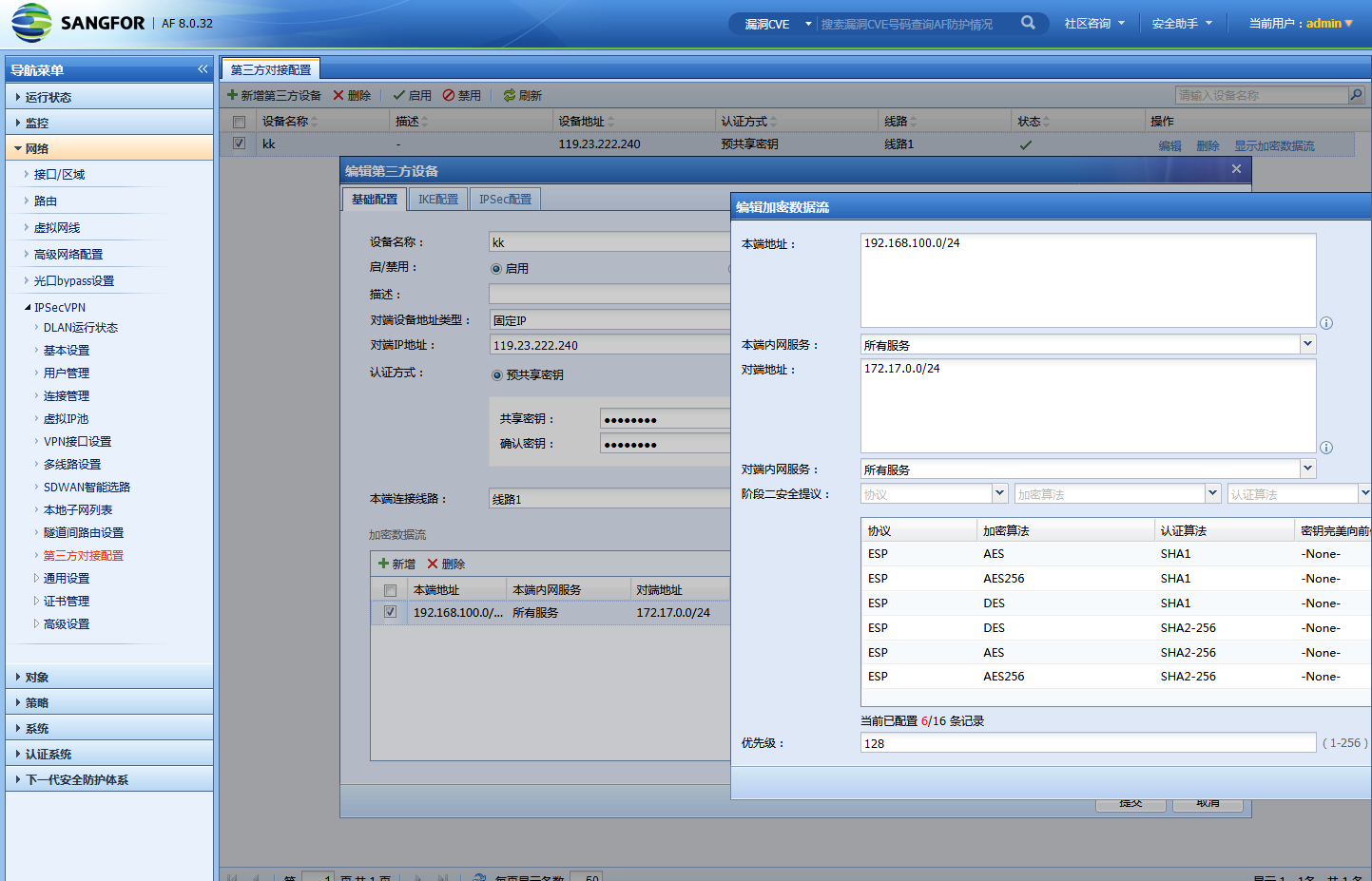
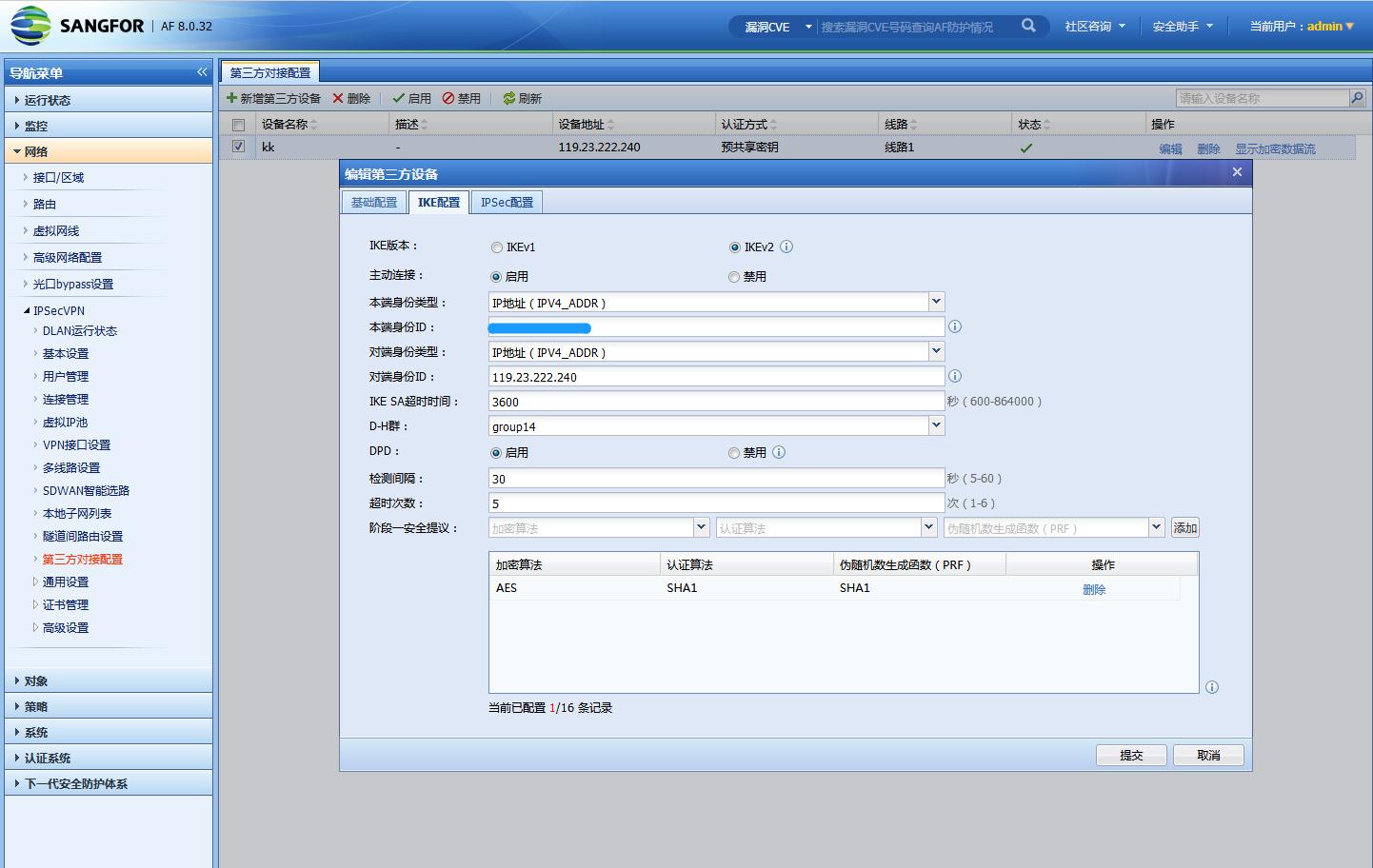
参考
https://help.aliyun.com/document_detail/110816.html
https://blog.csdn.net/weixin_43190642/article/details/122080246
https://www.cnblogs.com/shaoyangz/p/10345698.html
https://blog.csdn.net/qq_42760638/article/details/122042536
https://www.likecs.com/show-204025603.html
https://zhuanlan.zhihu.com/p/645066815











